
SAP Security
like you've never seen it before
100% seamlessly integrated in your SAP systems. Your personal coach to become an SAP Security master is here!
REQUEST A FREE DEMOTrusted by leading brands






A customer-centric platform
Customers around the globe rely on us. As a customer-centric company, we ensure our customers' needs are met and we welcome feedback at all times.

Customer Success Stories
- Don't believe us?
Trust those who actually use our platform.
Sanofi
- Replaced its enterprise SAP Security with SecurityBridge

Customer Success Stories
- Don't believe us?
Trust those who actually use our platform.
McCoy & Partners
- "With SecurityBridge‘s integration, McCoy can offer its customers comprehensive SAP domain protection.”

Customer Success Stories
- Don't believe us?
Trust those who actually use our platform.
MSP PASàPAS
- “From day one, we have been able to use SecurityBridge reports to alert our customers of their risky behaviors.”

Customer Success Stories
- Don't believe us?
Trust those who actually use our platform.
Schneider Electric
- Securing mission critical SAP Systems
worldwide

Customer Success Stories
- Don't believe us?
Trust those who actually use our platform.
Pharmaceutical
- "For SAP cybersecurity this is
the most advanced solution."

Customer Success Stories
- Don't believe us?
Trust those who actually use our platform.
Sport & Apparel
- "We selected SecurityBridge as it
represents next-generation technology."

Customer Success Stories
- Don't believe us?
Trust those who actually use our platform.
Insurance
- "SecurityBridge keeps our resources
lean and maximizes ROI."

“We selected SecurityBridge as the platform most comprehensive in functionality that is completely and seamlessly integrated within the SAP technology stack. SecurityBridge’s agile and holistic approach enables us to transition very quickly and smoothly.”
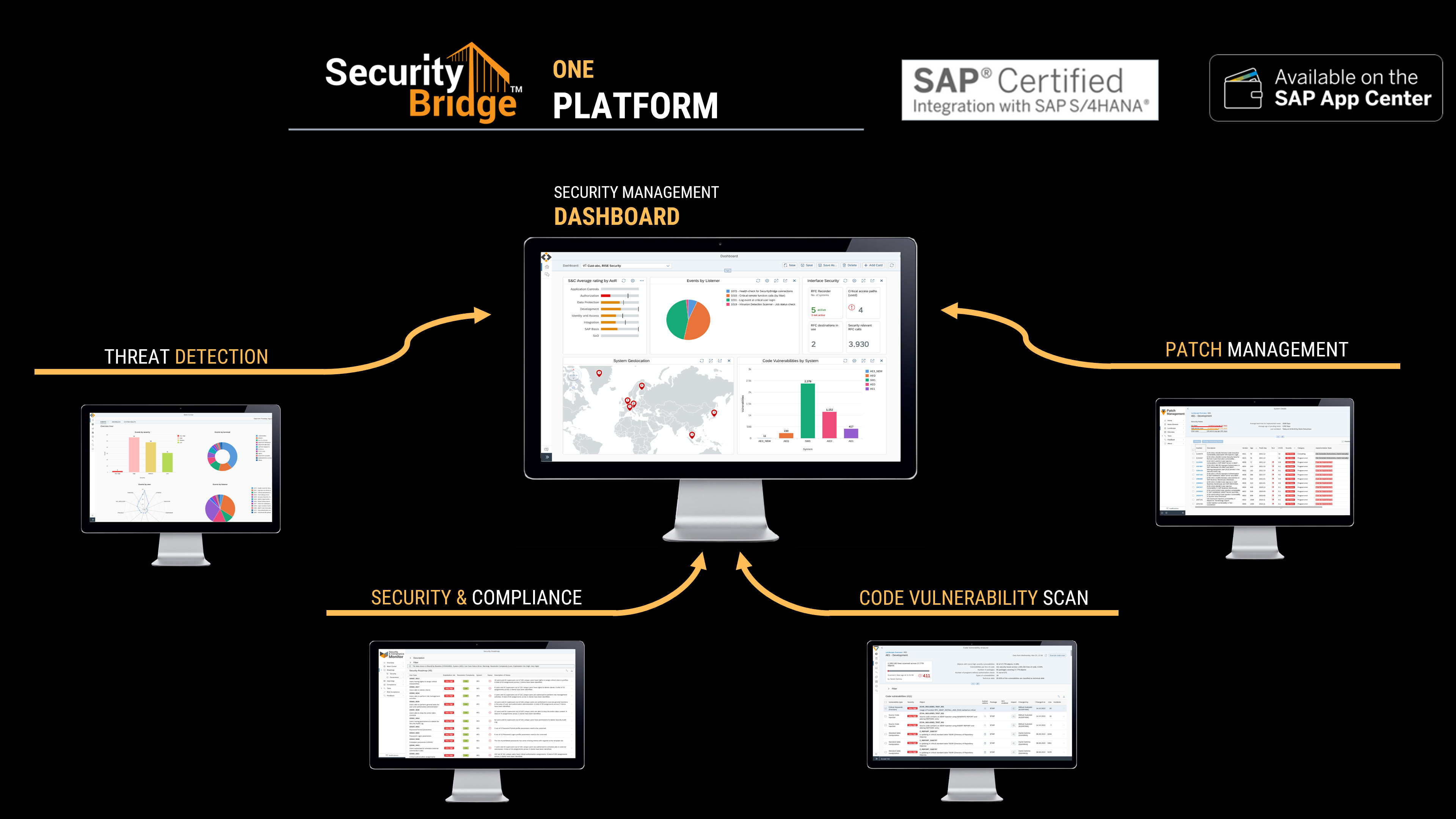
Protect Your Business with the only All-in-One Platform for SAP Security
Leverage the only security platform natively created in SAP for SAP users. Benefit from built-in full expertise, a holistic solution stack and automation framework. The SecurityBridge guided approach helps you to adopt sustainably SAP Security up to the highest level. By integrating the SecurityBridge Platform in all relevant IT operations processes, you ensure that your business is protected anytime against security breaches.
Ready to see how we can ensure your business is protected against potential security breaches?
Set It Up And Keep Going
- SAP Security Knowledge Base
- Specific quick wins for SAP system hardening
- Identity Protection to prevent SAP user ID misuse
- Threat Detection with default SAP protection template
Define Baseline & Execute Your Roadmap
- Security & Compliance Baselines (SOX, NIST, DSAG, etc.)
- Smart Roadmap for cleansing (high risk/low effort)
- Efficient Patch Management based on severity and impact
- Security Reporting
- Incident Management for SAP
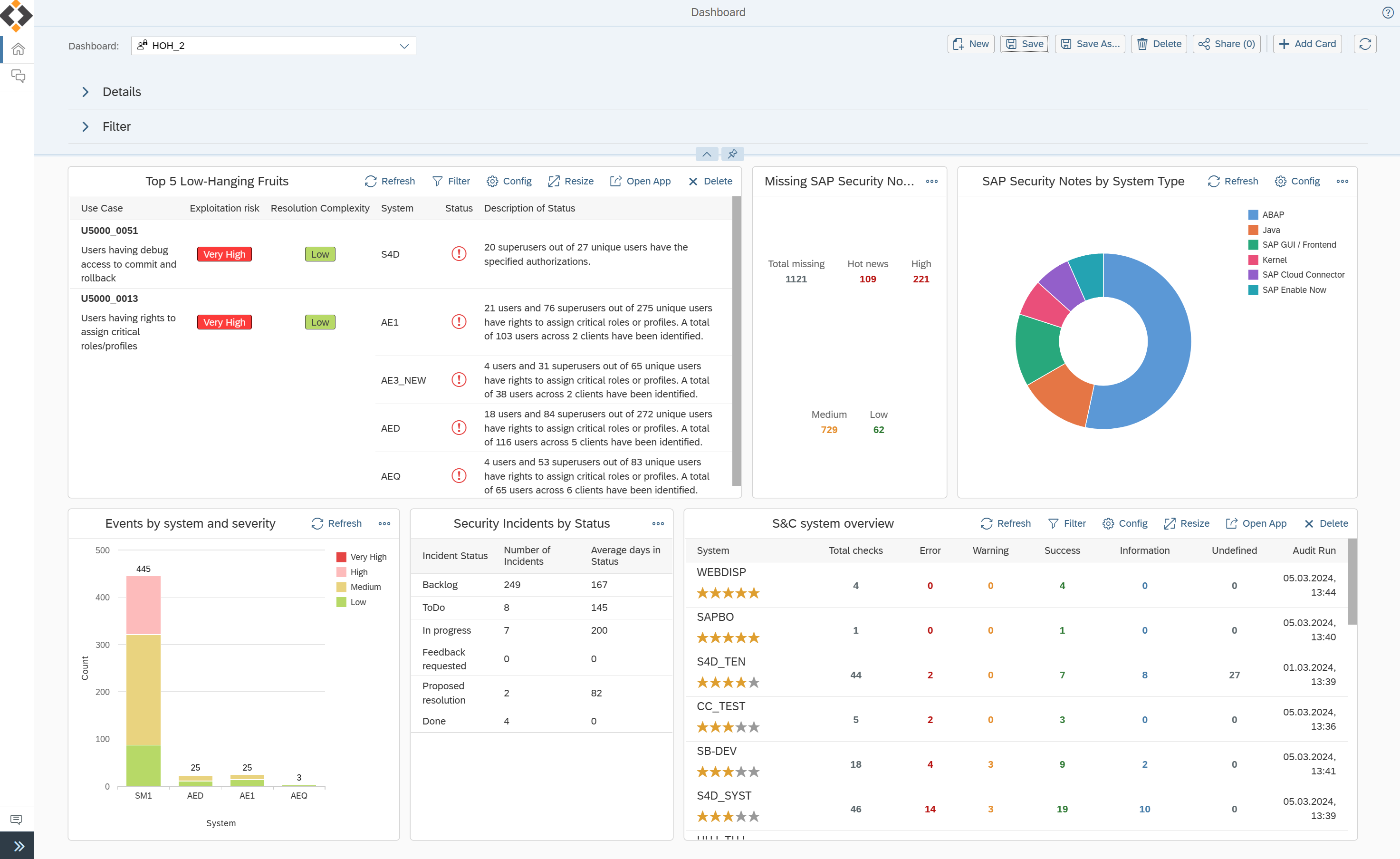
Scale-up Your SAP Security Posture
- Code Vulnerability Analyzer for custom code & technical debt
- Work packages for S&C and code vulnerability cleansing.
- Management Dashboard
- Interface Traffic Monitoring and HyperLogging for anomaly and Zero Day Threat Detection
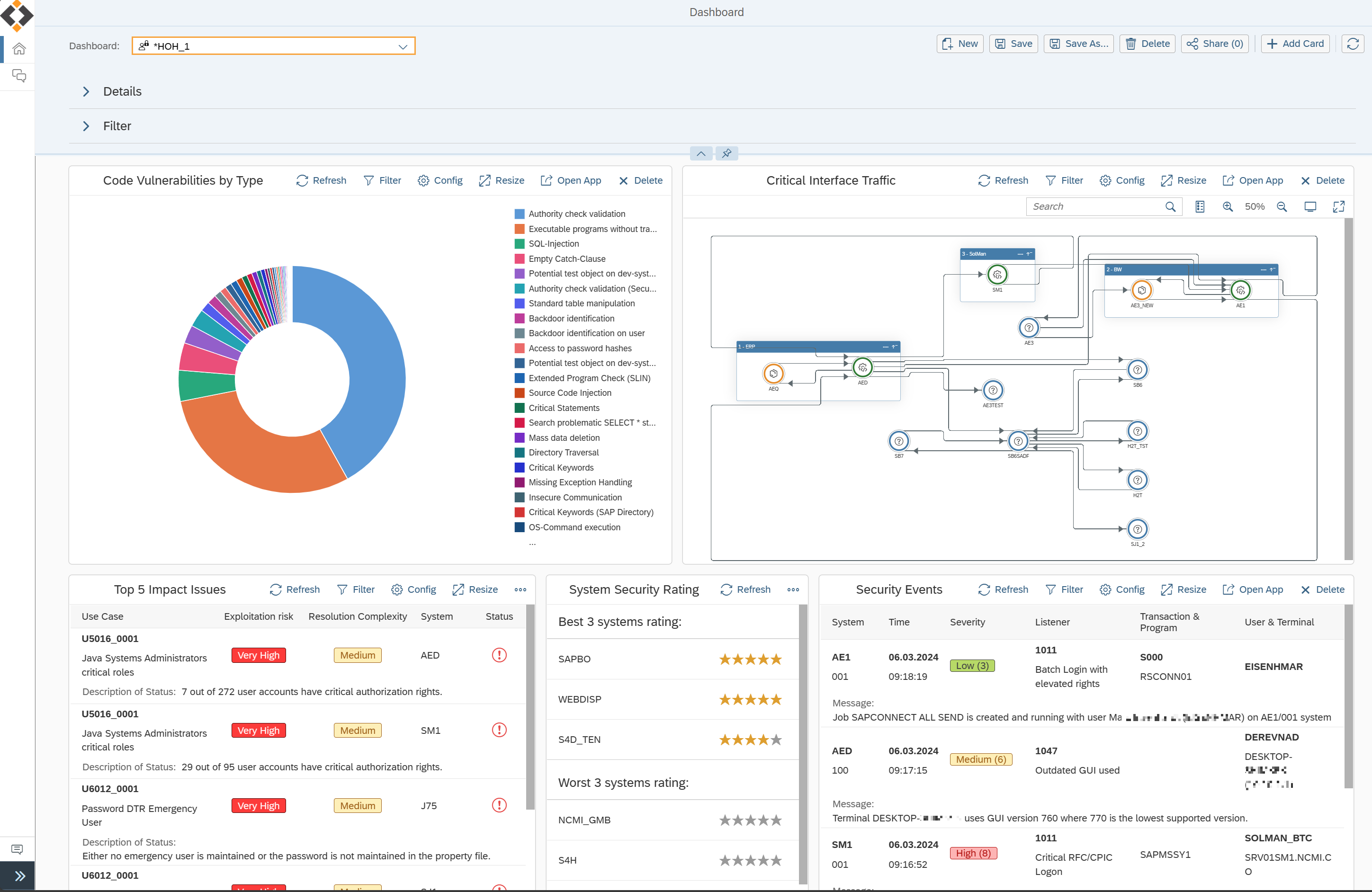
Aim For A Sustainable SAP Security
- Feed SAP Security events into SIEM / SOC
- Scanning new custom code with Transport Security
- Implement Risk Acceptance Process
- Automate Patch Management Process
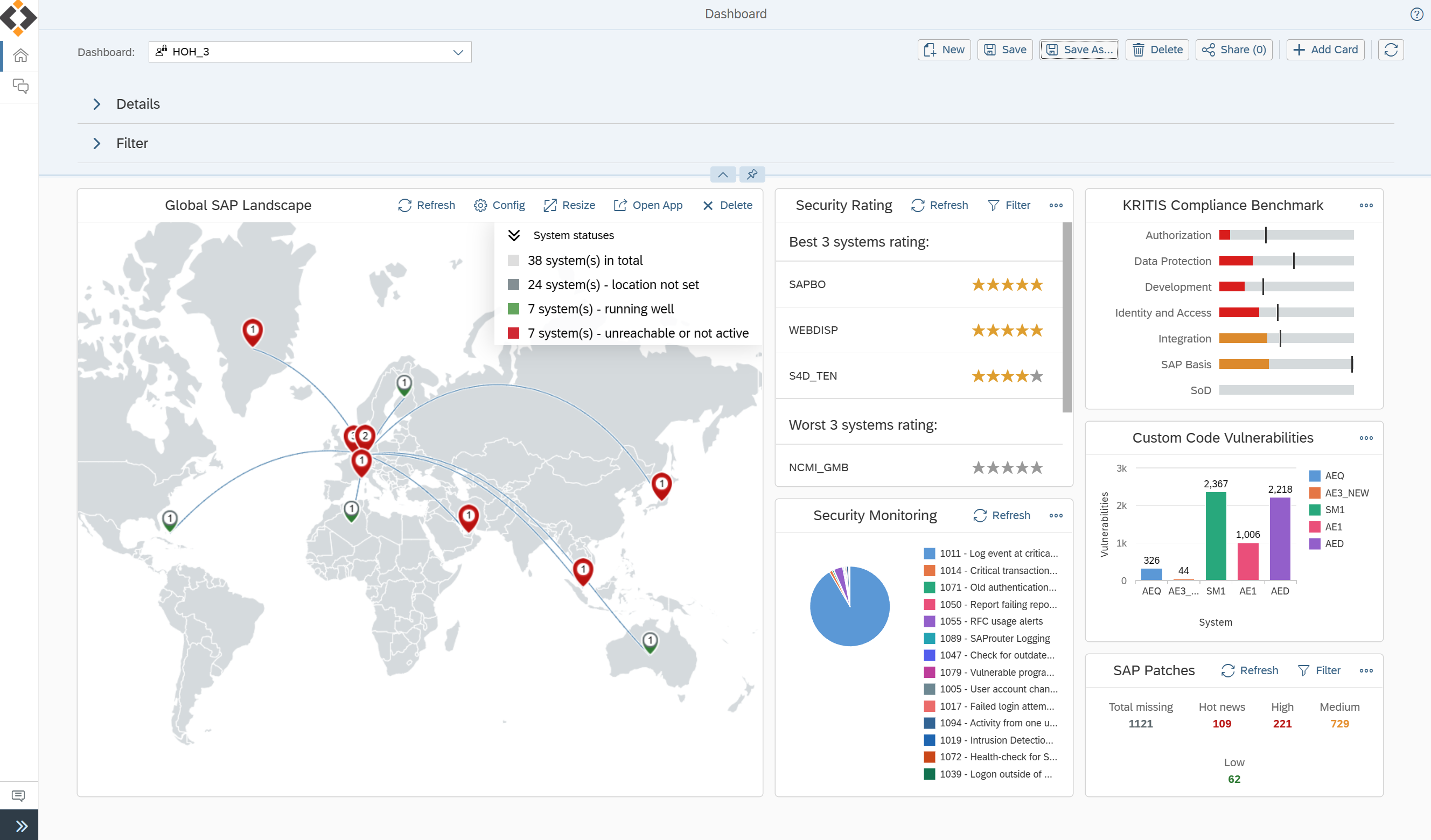
Establish Your SAP Security Process
- Enhance your GRC process by Privileged Access and Violation Management
- SAP Security integration with ITSM processes
- Establish SAP Security in the Software Lifecycle Management
- Perform compliance benchmarks and improve continuously
Start
Set It Up And Keep Going

- SAP Security Knowledge Base
- Specific quick wins for SAP system hardening
- Identity Protection to prevent SAP user ID misuse
- Threat Detection with default SAP protection template
Walk
Define Baseline & Execute Your Roadmap

- Security & Compliance Baselines (SOX, NIST, DSAG, etc.)
- Smart Roadmap for cleansing (high risk/low effort)
- Efficient Patch Management based on severity and impact
- Security Reporting
- Incident Management for SAP
Run
Scale-up Your SAP Security Posture

- Code Vulnerability Analyzer for custom code & technical debt
- Work packages for S&C and code vulnerability cleansing.
- Management Dashboard
- Interface Traffic Monitoring and HyperLogging for anomaly and Zero Day Threat Detection
Finish
Aim For A Sustainable SAP Security

- Feed SAP Security events into SIEM / SOC
- Scanning new custom code with Transport Security
- Implement Risk Acceptance Process
- Automate Patch Management Process
Win
Establish Your SAP Security Process

- Enhance your GRC process by Privileged Access and Violation Management
- SAP Security integration with ITSM processes
- Establish SAP Security in the Software Lifecycle Management
- Perform compliance benchmarks and improve continuously
Partners & Alliances
A proud partner of leading brands















Our partner network
Seize the opportunity to join our Partner ecosystem, to secure your customer’s SAP systems and its custom code. Capture a hyper-growth/untapped market, to deliver the most advanced security available for SAP customers, and generate revenue!
Become a partner
“The expansion of our partnership with SecurityBridge is an important step in complementing our portfolio. It will help us strengthen our position in a dynamic market environment and underpin our leading role as SAP Partner.”
Where you've heard from us










As a trusted provider of SAP security solutions, we are committed to continuous innovation to address the ever-growing threat of cyberattacks. We protect our customers and work with strong partners to respond quickly to changes in the global risk profile for SAP customers.
Discover Our Press Center
How much can you save?
Calculate an individual business case for SecurityBridge usage and related improvement.
TRY OUR BUSINESS CASE CALCULATOR

Gartner
peerinsights