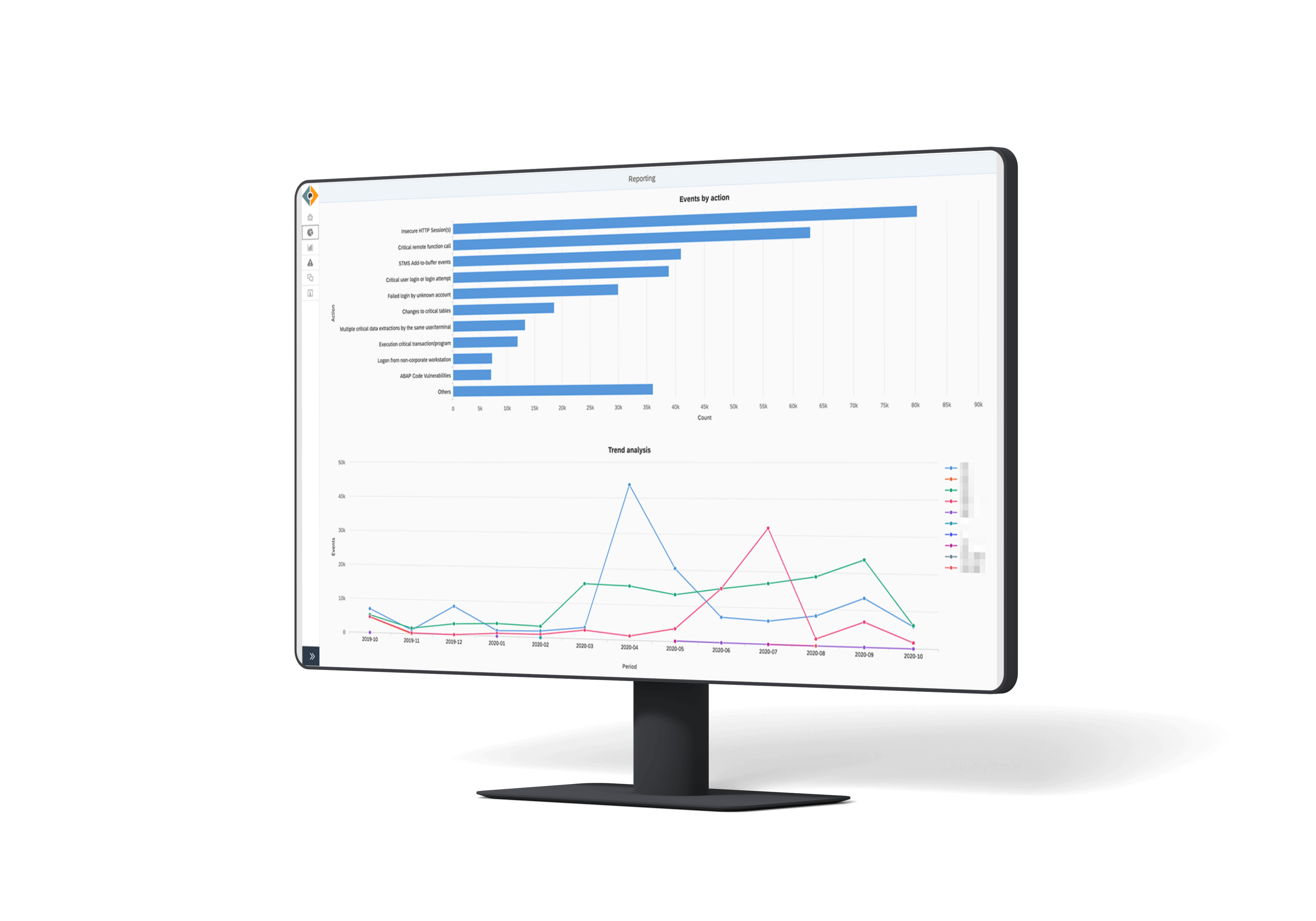
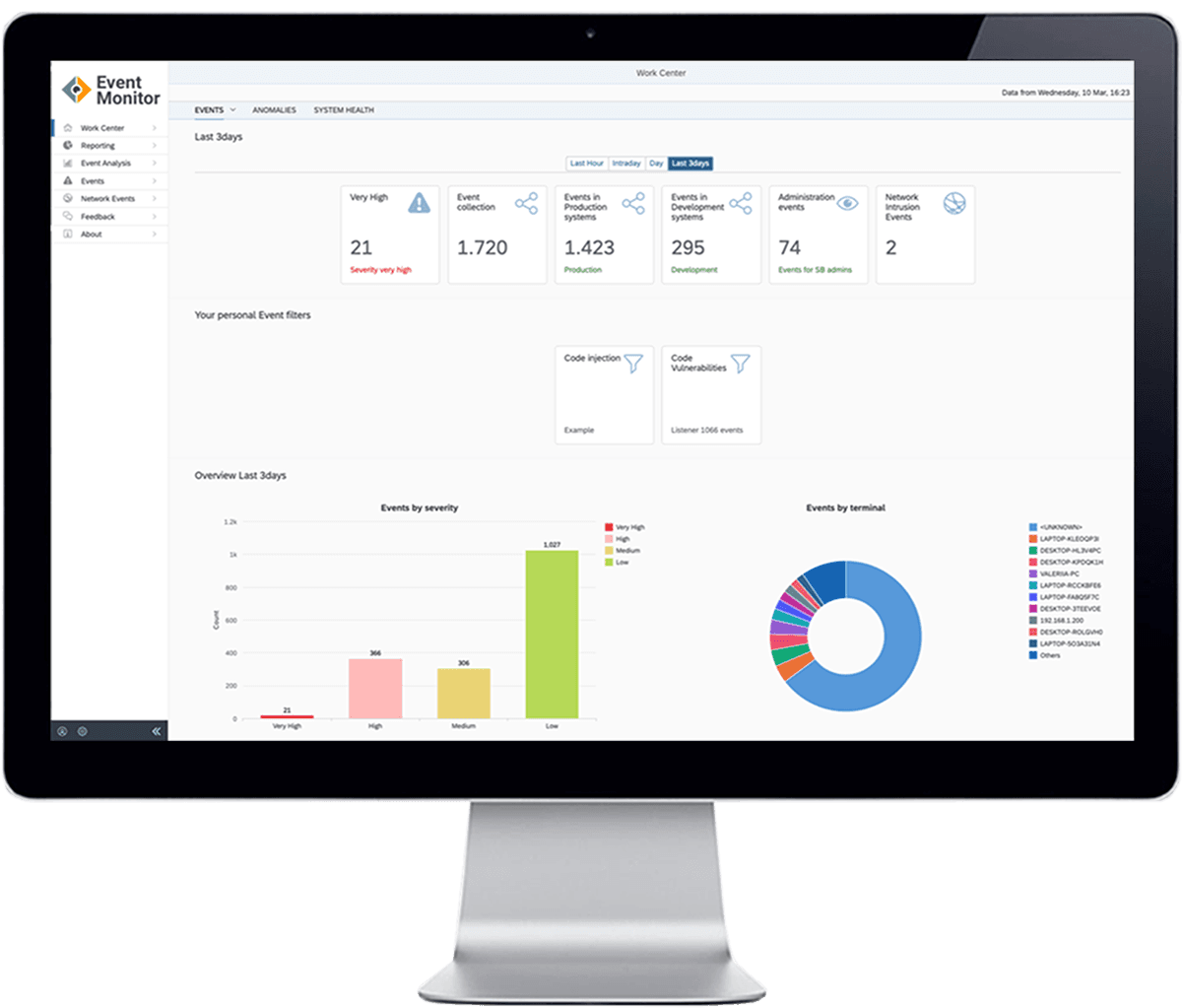
5 Steps for Kick-starting Holistic SAP Security in 1 Day
SAP Security teams can kick-start a comprehensive security platform and gain significant improvements already within a day. What they need is a holistic platform and a guided approach to SAP Security.