
SAP Vulnerability Management vs SAP Patch Management
This article explores the differences between the 2 processes and how they can help bolster the security of SAP systems.
Protect your SAP applications with our comprehensive SAP security solution that addresses all your security needs. Our platform seamlessly integrates within your SAP environment and provides actionable insights in hours. Reduce the risk of data breaches and compliance violations with our trusted solution.
“We selected SecurityBridge as the platform most comprehensive in functionality that is completely and seamlessly integrated within the SAP technology stack. SecurityBridge’s agile and holistic approach enable us to transition very quickly and smoothly.”
“The expansion of our partnership with SecurityBridge is an important step in complementing our portfolio. It will help us strengthen our position in a dynamic market environment and underpin our leading role as SAP Partner.”

EVP, Global Innovation & IP, Global SAP Alliances & Region NEE
NTT DATA Business Solutions AG
Introducing the first and only holistic, natively integrated SAP security product that addresses all aspects necessary to protect organizations against cyber threats. The SecurityBridge Platform identifies SAP vulnerabilities and risks, providing mitigation measures to safeguard your organization’s critical assets. With our product, you can rest assured that your business is protected against potential security breaches.
Fast implementation, rapid discovery, actionable insights. Advanced SAP security technology includes anomaly detection for identifying sophisticated threats.
Eliminate false positives, optimize Security Analyst’s effort with a specialized Security Operation Center (SOC) integration for SAP.
Experience truly integrated real-time threat monitoring with SecurityBridge for SAP Threat Detection. Evolving results increase awareness of your organization’s threat posture.
Streamline your SOC team’s focus with SecurityBridge, the easy-to-maintain, deploy, and install SAP security solution.
Experience a unified platform with SecurityBridge. Our open architecture enables intelligent sharing of findings across all modules.
Streamline your security operations with the SAP SIEM connector. Our platform offers seamless, out-of-the-box integration with leading SIEM products.
Automate Patch detection with SecurityBridge. Our platform detects missing patches, including SNotes and SAP Kernel Patches, for a timely implementation.
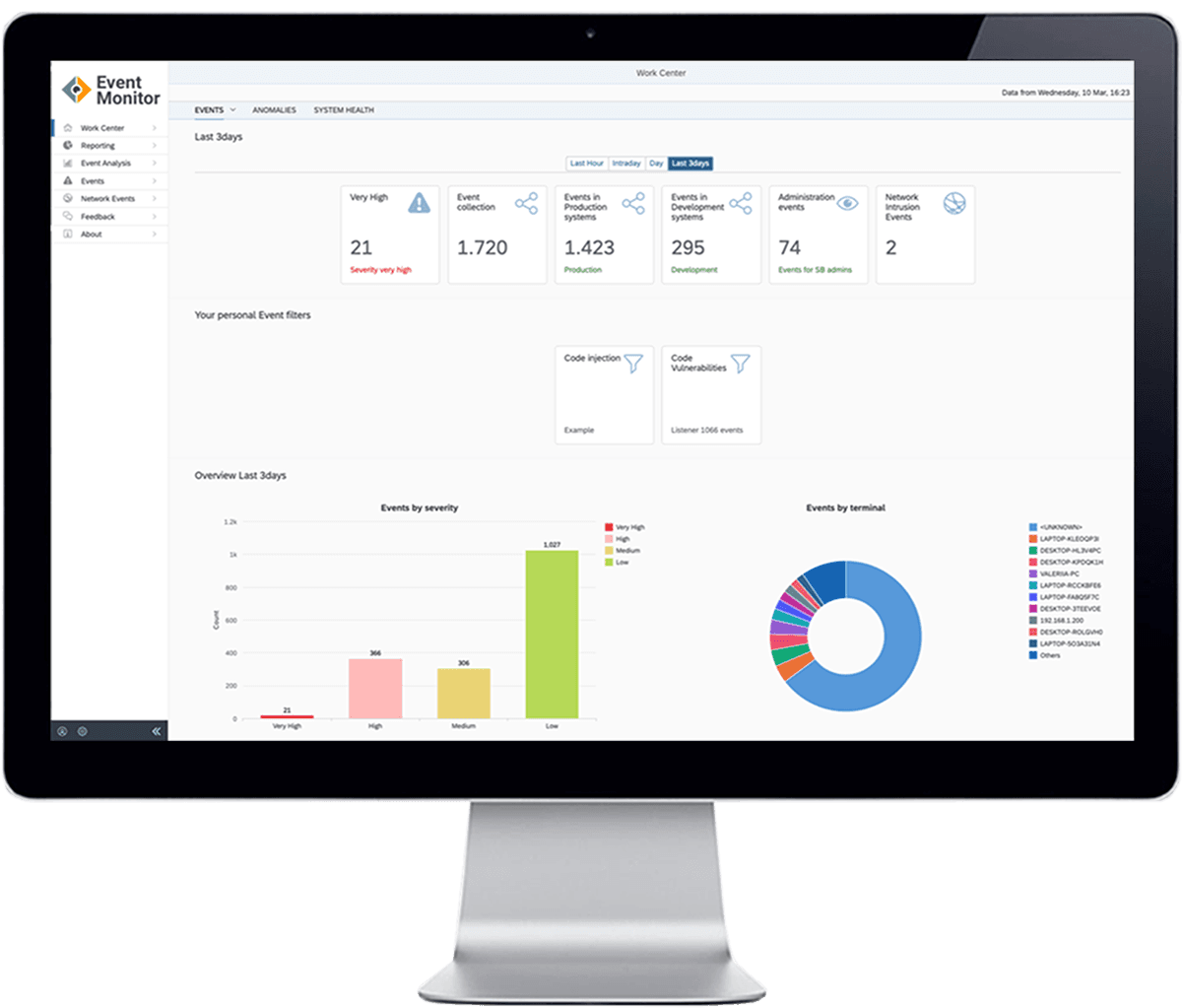
Get a single source of truth with our Dashboard, providing comprehensive insights in one place.
Report security incidents with one click, document risk acceptance inline, and access the integrated knowledge base.
Ready to meet security like never before?
Calculate an individual business case for SecurityBridge usage and related improvement.
Reinforcing the security of the global organization.
Resilience, security, and responsiveness are your core operational requirements. Our solutions help you to deliver your…
SecurityBridge integrates with Fortinet’s FortiGate a NextGen Firewall to increase the accuracy of detecting attacks on SAP applications.
The Platform receives frequent updates of attack detection patterns, compliance rules, and SAP security features. In our publications, we also inform you about active threats or security trends for SAP customers.

This article explores the differences between the 2 processes and how they can help bolster the security of SAP systems.

We are expanding our operation in the APAC region and are looking for an experienced Sales & Partner Manager to join our team in Singapore. The ideal candidate will have at least 5 years of experience in sales, with a focus on software sales, SAP security, or cybersecurity.

As a Pre-Sales Consultant at SecurityBridge, you will be instrumental in our rapid expansion within the APAC region. You will directly contribute to the growth of our innovative SAP security solution, SecurityBridge.

For April 2024, 10 new Security Notes have been released and 2 have been updated. What stands out is that there are no ‘Hot News’ notes in this release. But let that not be a reason to ‘lower your guard’! We explore some interesting highlights below.

Recently, we have seen the release of several SAP Security notes that address the so-called ‘Rapid Reset Attack’ vulnerability. In this blog, we will zoom in on this vulnerability, look at how it affects SAP systems, and what counter measures can be taken.

Kontron und SecurityBridge schließen eine strategische Partnerschaft für eine verbesserte IT-Sicherheit von SAP-Systemen ab.
ONE-STOP SHOP PLATFORM FOR SAP SECURITY
ABAP, HANA, JAVA, SAP CLOUD – We cover it all